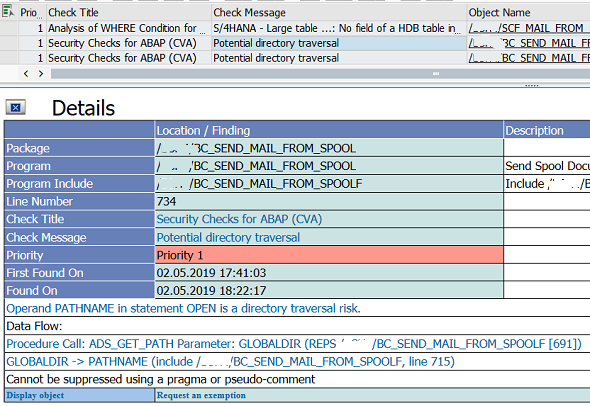
Security Checks for ABAP (CVA): Potential directory traversal
If programmers run ATC checks for security CVA on ABAP codes where Open command is used and its operand pathname is not validated by function module FILE_VALIDATE_NAME before use, ATC check will identify the case as Potential directory traversal. The CVA finding is listed in the result with message "Operand PATHNAME in statement OPEN is a directory traversal risk"
Security Checks for ABAP (CVA)
Potential directory traversal
Priority 1
Operand PATHNAME in statement OPEN is a directory traversal risk.
Data Flow:
Procedure Call: ADS_GET_PATH Parameter: GLOBALDIR (REPS ZBC_SEND_MAIL_FROM_SPOOLF [691])
GLOBALDIR -> PATHNAME (include ZBC_SEND_MAIL_FROM_SPOOLF, line 715)
When I click on the link within "Object Name" column of the ATC finding result list, it navigates me to the ABAP code causing CVA error. Here is the ABAP code that causes CVA issue.
CONCATENATE globaldir '/' partfilename INTO pathname.
...
OPEN DATASET pathname FOR INPUT IN BINARY MODE.
To resolve this issue ABAP developers have to validate the file name identified with "pathname" using function modulel FILE_VALIDATE_NAME and use the returning physical filename.
Add a new code block before "OPEN DATASET" code line.
First of all, concatenate file path parts into a different string variable instead of "pathname".
So we will create a new string variable and store the fully qualified path in this new string variable as follows.
DATA lv_pathname(256).
CONCATENATE globaldir '/' partfilename INTO lv_pathname.
Then for ABAP function module FILE_VALIDATE_NAME input and output parameters, create following two variables and assign the file path into input variable.
Finally call the ABAP function module for validating the full path of the file
DATA iv_file LIKE filename-fileintern.
DATA ov_path(256) TYPE c.
MOVE lv_pathname TO iv_file.
CALL FUNCTION 'FILE_VALIDATE_NAME'
EXPORTING
logical_filename = iv_file
CHANGING
physical_filename = ov_path
EXCEPTIONS
logical_filename_not_found = 1
validation_failed = 2
OTHERS = 3.
IF sy-subrc = 0.
pathname = ov_path.
ELSE.
* Implement suitable error handling here
ENDIF.
CLEAR lv_pathname.
You see, after file path validation is completed by FILE_VALIDATE_NAME ABAP function module, ABAP programmer can use the changing parameter value as an input to the "OPEN DATASET" command as follows.
OPEN DATASET pathname FOR INPUT IN BINARY MODE.
This will resolve the CVA security finding "Potential directory traversal" by ATC.
