Code Inspector Call Executable Program Check for ABAP Submit Report
SAP provides tools like ABAP Test Cockpit (aka ATC) or Code Inspector that can be used by ABAP developers to find Submit report commands which are vulnerable using call executable program checks, and help programmers for secure coding in custom ABAP code developments.
To execute an ABAP program using SUBMIT statement is a vulnerable command especially your ABAP developer is using dynamic ABAP programming. Using ABAP Test Cockpit aka ATC or Code Inspector tool, SAP professionals can create a list of vulnerable ABAP code fragments to provide a more secure software in your SAP system.
Recently when I run ATC (ABAP Test Cockpit) on my ABAP code developments, a common critical statement listed for security was "Call Executable Program ..."
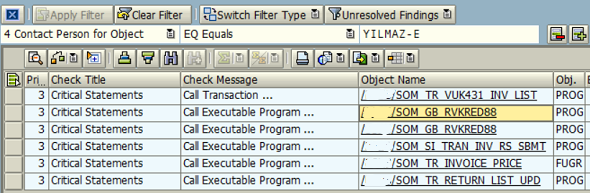
Especially if you are developing dynamic ABAP for calling executing ABAP program with Submit report statement, it is a critical security vulnerability for your SAP system environment.
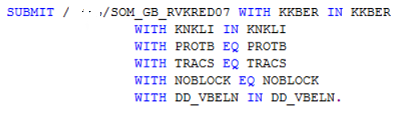
Unfortunately, it is not very easy to get rid of these ATC messages for SUBMIT program ABAP command in some cases.
I want to summarize a few methods that can be done for more secure coding with SUBMIT here.
Explicitly check authorization for ABAP program,
authority-check on S_DEVELOP can be called before executing SUBMIT statement,
For S_DEVELOP, ABAP programmers can refer to SAP Community WIKI reference.
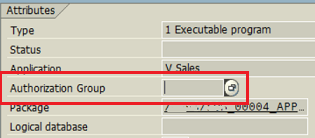
Use the Authorization Group attribute for your ABAP program which is used in SUMBIT statement.
Try to use ABAP class CL_ABAP_DYN_PRG whitelist string or whitelist table methods to test the validity of dynamically provided program names in your ABAP codes.
If all above does not help, and as an ABAP developer you are sure it is safe to use the SUBMIT to execute an other ABAP program, you can use the pseudo comment #EC CI_SUBMIT for Code Inspector checks as follows.
SUBMIT ZGB_RVKRED07 WITH KKBER IN KKBER
WITH KNKLI IN KNKLI
WITH PROTB EQ PROTB
WITH TRACS EQ TRACS
WITH NOBLOCK EQ NOBLOCK
WITH DD_VBELN IN DD_VBELN. "#EC CI_SUBMIT
For using ABAP Submit report command, programmers can refer to online ABAP tutorial ABAP Submit Report to Run another ABAP Program for more information and sample code.
