How to Execute Spring Vulnerability Scanner on AWS Linux AMI
In this tutorial, I want to share how AWS developers can download and execute Spring Vulnerability Scanner from GitHub project on an AWS EC2 instance based on Linux.
If you want to scan your servers to identify if your applications are vulnerable for the SpringShell CVE-2022-22965 vulnerability, you can follow the steps in this guide on an AWS Linux instance.
For more about the Local Spring Vulnerability Scanner, you can check the readme documentation and the instructions for the vulnerability scanner on Github project
I want to share how AWS developers can download and run the Spring vulnerability scanner on EC2 instances.
Connect to EC2 instance on AWS Management Console using Session Manager
Create a new folder where you will later download the Spring Vulnerability Scanner using mkdir command
sudo mkdir SpringVulnerabilityScanner
![]()
Now enter the folder you have created
cd SpringVulnerabilityScanner
![]()
We can now download the executable scanner file into this current directory by executing below command
wget https://github.com/hillu/local-spring-vuln-scanner/releases/download/v0.1.1/local-spring-vuln-scanner
If you get a "Permission denied" error message you can execute the same command with sudo as follows
sudo wget https://github.com/hillu/local-spring-vuln-scanner/releases/download/v0.1.1/local-spring-vuln-scanner
When I execute above command on a sample EC2 instance, I got following message indicating that the scanner file is successfully downloaded into the working directory.
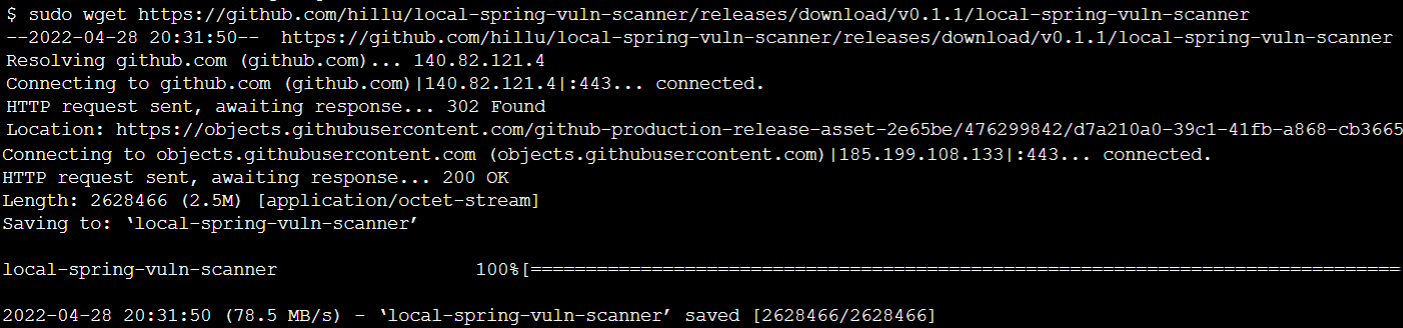
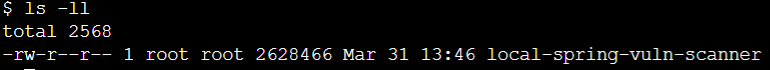
When you display the permissions of the downloaded scanner file you will see it is set to read only
ls -ll
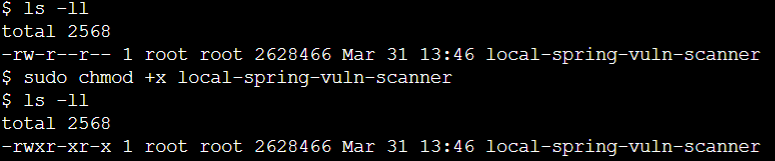
We can now change the file attributes from read only file to executable file using chmod
sudo chmod +x local-spring-vuln-scanner
Let's now validate the change
ls -ll
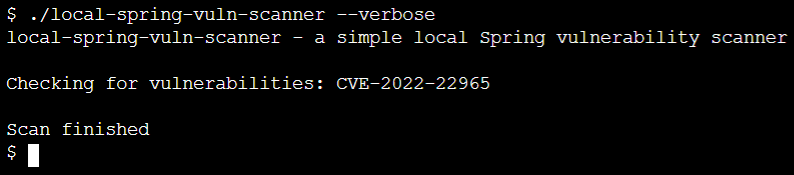
Let's now run the scanner file by running below command within the directory where you downloaded the Spring Vulnerability scanner
./local-spring-vuln-scanner --verbose
Please note that while running the spring vulnerability scanner file you can provide following attributes which is explined in detail at GitHub Local Spring Vulnerability Scanner
$ ./local-spring-vuln-scanner [--verbose] [--quiet] \
[--exclude /path/to/exclude …] \
[--scan-network] \
[--log /path/to/file.log] \
/path/to/app1 /path/to/app2 …
If a vulnerable component is detected by the scanner, those vulnerable components will be listed within the output data
Hope this short guide is useful for who try to execute the Spring Vulnerability Scanner file on their EC2 instances on AWS platform.
