Enable Amazon Detective Service on AWS Management Console
Amazon Detective is one of AWS services under Security, Identity and Compliance category which enables AWS administrators, operation engineers easily investigate, analyze, and quickly identify the root cause of potential security issues or suspicious activities on the active AWS account. Amazon Detective collects log data about your AWS resources automatically from different resources like the AWS resource itself, AWS CloudTrail logs, VPC Flow logs and Amazon GuardDuty. The collected log data is processed by Amazon Detective service automatically using machine learning, statistical analysis, and graph theory. Then to enable the AWS professionals to investigate potential security issues, Amazon Detective visualizes the findings for a faster and efficient security investigation.
It is easy to start with Amazon Detective AWS service.
Amazon Detective will start collecting log data from the AWS resources in your account automatically.
Then based on the collected logs, Amazon Detective service will provide visualizations to assist AWS processed for security investigations.
If you want to try Amazon Detective service and have a look at the findings and how it can help you to investigate any potential security issue, you can benefit from the 30-day free trial chance.
First of all, you should enable Amazon Detective on AWS management console before you start to analyze and investigate security issues.
As I noted before, Amazon Detective will analyze:
CloudTrail Logs,
VPC Flow Logs, and
Amazon GuardDuty Findings
The log data is collected continuously. It is analized and organized into a graph model which is modified continuously to easily identify relations and root causes of security issues.
Amazon Detective service is integrated with other security services provided by AWS like Amazon GuardDuty and AWS Security Hub as well as partner security products. This integration enables cloud professionals click on an "Investigate" button or link from each of those AWS service consoles to the findings and analysis results of Amazon Detective service.
The visualizations of Amazon Detective enables users to have a quick sense about a potential security issues and drill down into results for detailed information.
To start using Amazon Detective, on the AWS Management Console go to the service dashboard and press "Get started" button.
![]()
This button will lead the cloud professionals to following page where it is recommended to use the same account with other majos AWS security services.
Align administrator accounts (recommended)
Administrator account alignment allows an account to select a finding in Amazon GuardDuty or AWS Security Hub and pivot seamlessly into Detective. Once in the Detective console, an administrator account can archive GuardDuty findings.
To enable this capability, we recommend using the same account as the administrator across GuardDuty, Security Hub, and Detective. If this is not possible, you can set up a cross-account role to allow multiple accounts to act as the administrator across these services.
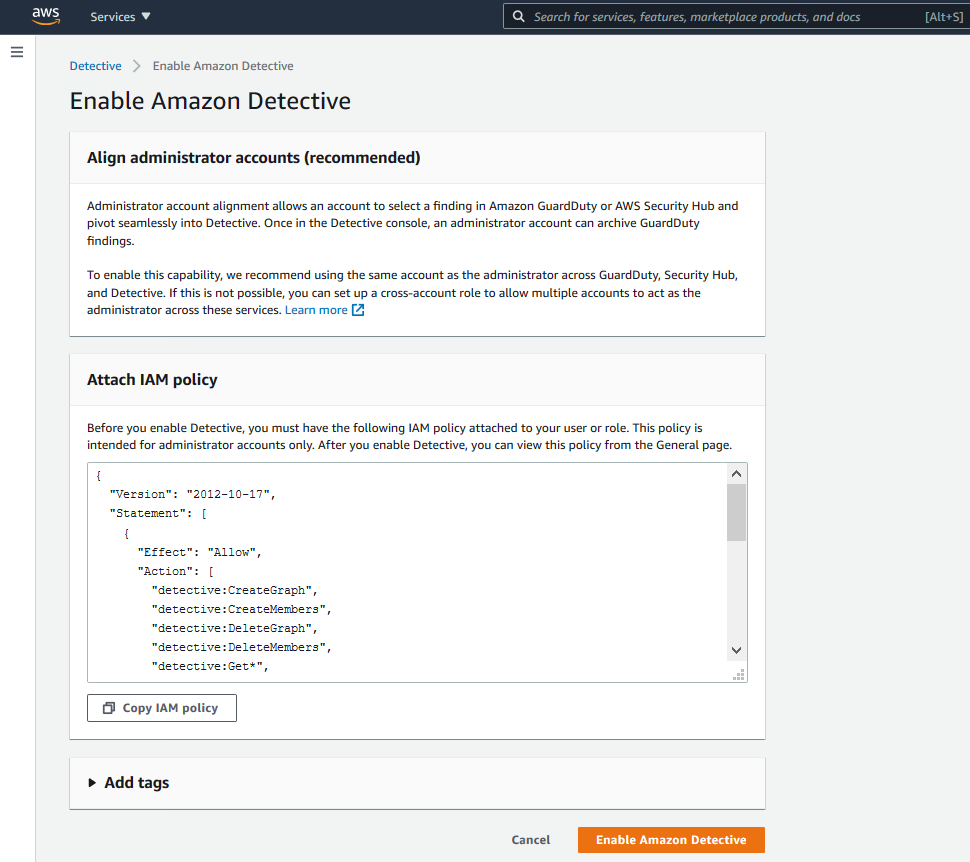
Before enabling Amazon Detective, following IAM policy should be attached to the AWS IAM user or IAM role.
The below IAM policy to be attached is for administrator accounts which enables use of Amazon Detective service API actions, GuardDuty actione and Amazon Organizations for managing sub-accounts or member accounts.
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"detective:CreateGraph",
"detective:CreateMembers",
"detective:DeleteGraph",
"detective:DeleteMembers",
"detective:Get*",
"detective:ListGraphs",
"detective:ListMembers",
"detective:ListTagsForResource",
"detective:SearchGraph",
"detective:StartMonitoringMember",
"detective:TagResource",
"detective:UntagResource",
"guardduty:ArchiveFindings",
"guardduty:ListDetectors",
"organizations:DescribeOrganization",
"organizations:ListAccounts"
],
"Resource": "*"
}
]
}
To continue click the Enable Amazon Detective button.
Once the Amazon Detective is enabled successfully it will start collecting logs data about your resources in the AWS account and start ingesting all these data into the Amazon Detective service dashboard.
Other AWS accounts can be also merged into the Amazon Detective console dashboard if you wish to display all security investigation data of your organization's accounts in one place.
Other member AWS accounts can be invited for the Amazon Detective of the parent account.
Once data is collected and analyzes, the Amazon Detective Summary page will guide cloud security engineers as a starting point for investigating an security issue.
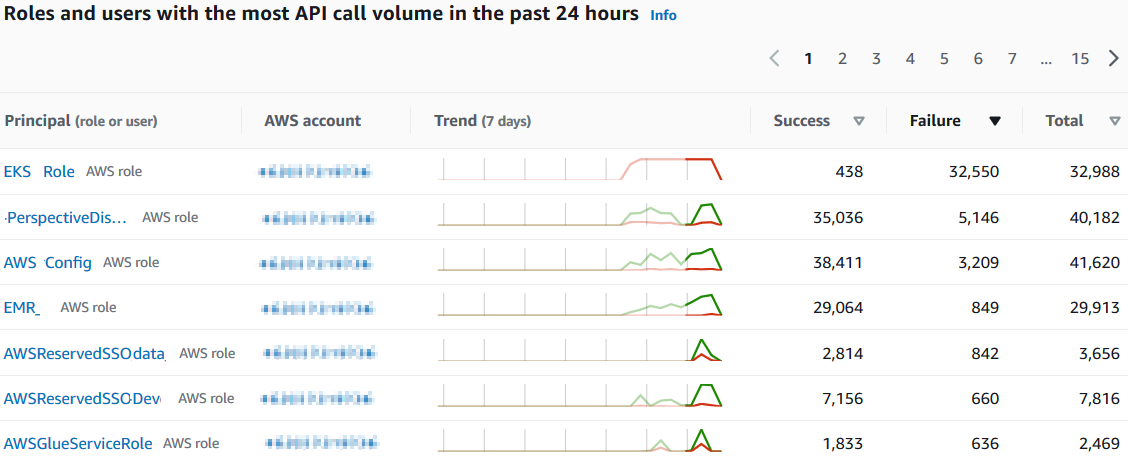
As a sample, a section within Amazon Detective will list the IAM roles and users with the most API call volume in the last 24 hours period. A high number of API calls from a certain IAM user or role may indicate an issue of a breached user credentials for example.
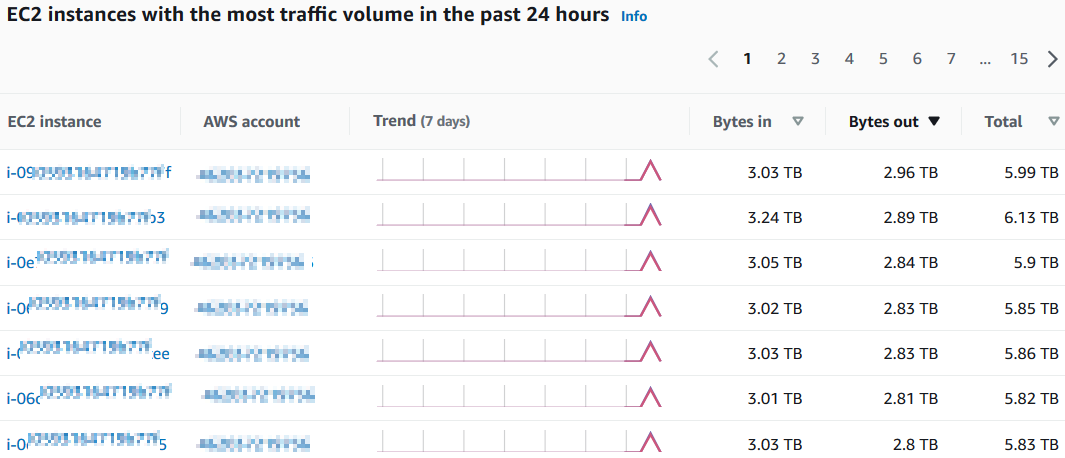
Another interesting and which I find useful most is the list of AWS EC2 instances with the most traffic volume in the past 24 hours. Here on the list, AWS professionals can see the inbound and outbound traffic volume for each EC2 instance sorted by descending traffic volume.
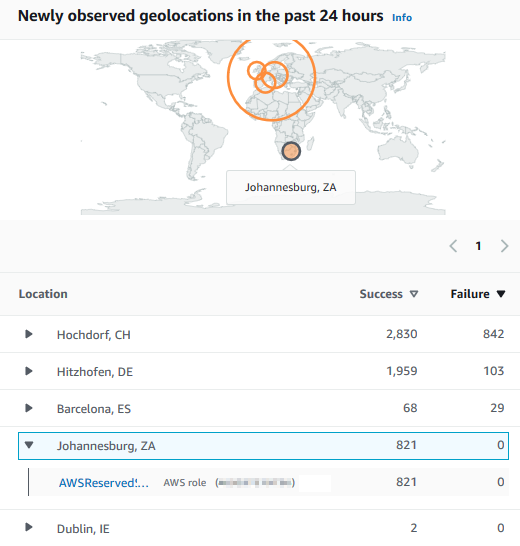
Another visualization that will help AWS cloud security engineers to detect and investigate security issues is the newly observed geolocations where the any API activity related with member AWS accounts in the past 24 hours. On the world map, you are displayed new geolocations with activities so you can filter those new places where your AWS account is reached and operations took place.
If you are interested specifically in a certain AWS EC2 instance, you can search for that specific EC2 instance using its ARN (Amazon Resource Name) or EC2 instance ID value on the Amazon Detective dashboard. That search results will guide the AWS cloud users to that EC2 instance specific page where following details can be viewed visually.
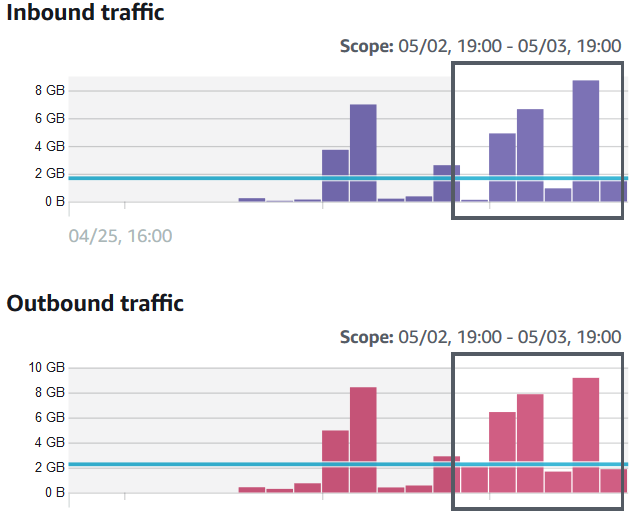
Overall VPC flow volume
Overall VPC flow volume displays the overall traffic volume of VPC flow data into and out of that specific EC2 instance.
A good feature of this visualization is that the in/out traffic graph is displayed with compared to a baseline which is calculated by average traffic from the last 45 days.
AWS users will be provided an Inbound traffic and Outbound traffic on a graph with baseline (or average) for 4-hours time periods within a day.
Keeping the investigating security issues benefit a side, even only this value (in and out of an EC2 instance traffic with baseline) can provide AWS engineers or architects an insight about their AWS EC2 instance usage and provide you a baseline for scheduled scaling for future.
Among other figures "Distinct IP addresses over time" is also interesting.
This figure shows the distinct number of IP addresses that connected to the observed Amazon EC2 instance during each time interval.
By looking at this graph the normal distribution of consumers or connections of the EC2 server can be identified.
A significant increase in the amount of traffic or in the number of distinct IP addresses might be evaluated as an alarm statu sof a distributed denial of service (DDoS) attach for internet facing or public EC2 servers.
On the opposite site, a significant drop pattern might be a signal of connectivity loss or a problem on the application running on the EC2 instance.
Not only EC2 instances, but also the IP addresses of your clusters can be queried to to visualize the inbound and outbound traffic. For example, you can use your AWS cloud data warehouse cluster's (Amazon Redshift DWH) leader node to identify the baseline of the inbound traffic (connection requests, SQL queries, data ingestion) and for the outbound traffic (data read by SQL queries).
To understand in detail the features of Amazon Detective and how to use Amazon Detective to investigate potential security issues, Basics of Amazon Detective training can be taken by AWS security professionals.
