How to Connect AWS EC2 Instance using Session Manager
In this AWS tutorial, I want to show cloud engineers to connect to AWS EC2 instances using Session Manager without a SSH ports are opened and without any SSH keys. AWS Systems Manager Session Manager enables Amazon Web Services cloud platform developers and users to access to EC2 servers even if they are in private subnets without a requirement of a bastion host or SSH ports being enabled. Using AWS Session Manager, users can connect and execute commands on remote EC2 instances over a terminal screen launched within the browser screen. In this AWS EC2 tutorials, I want to show how the Session Manager can be used to connect EC2 instances easily.
Connecting to AWS EC2 Instance using Session Manager
When you connect to your AWS account using AWS Management Console, switch to the AWS ECS dashboard and display the list of your EC2 servers on Instances list.
Mark the checkbox next to the EC2 instance that you want to connect. Then click on the Connect button on the top right corner of the EC2 instances list.
In order to connect to your target AWS EC2 instance, AWS administrator, developer or cloud users can use any of the below options:
EC2 Instance Connect
Session Manager
SSH client
EC2 Serial Console
For this tutorial, we are dealing with the Session Manager options, because it is more secure and more simple than other options.
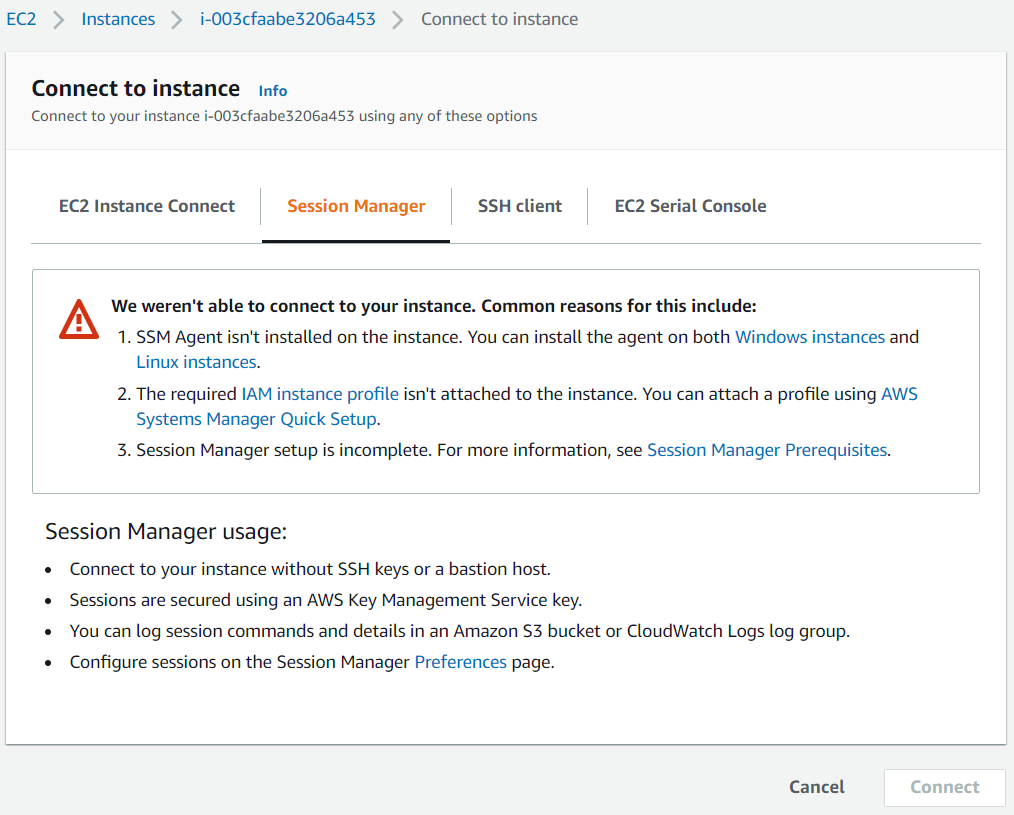
Of course as can be expected, there are some prerequisites to be fulfilled in order to use AWS Session Manager for connecting to a specific EC2 instance.
If you cannot connect to the target EC2 server, as noted on the screen, the main possible reasons can be:
1. SSM Agent isn't installed on the instance. You can install the agent on both Windows instances and Linux instances.
2. The required IAM instance profile isn't attached to the instance. You can attach a profile using AWS Systems Manager Quick Setup.
3. Session Manager setup is incomplete. For more information, see Session Manager Prerequisites.
If you are using the new Amazon AMI images while launching your EC2 instances then the SSM Agent is already installed. And in most cases, the reason is the IAM instance profile is not attached to the target EC2 instance that you are trying to conenct. In fact, IAM instance profile attachment is a process of creating an IAM policy to an IAM role which is assigned to your AWS EC2 server. We will cover these steps in following sections in this tutorial.
To summarize Session Manager enables cloud users to:
Connect to your instance without SSH keys or a bastion host.
Sessions are secured using an AWS Key Management Service key.
You can log session commands and details in an Amazon S3 bucket or CloudWatch Logs log group.
Configure sessions on the Session Manager Preferences page.
Create IAM Role with required IAM Profile for AWS Session Manager
Let's create the IAM Role which we will assign to AWS EC2 instance and will enable us to connect to that EC2 server.
Switch to Identity and Access Management (IAM) on AWS Management Console.
On the left menu of IAM Dashboard, go to Roles for the list of the existing IAM roles or creating a new role
Click on Create role
Select EC2 service among common use cases
Then attach the AmazonSSMManagedInstanceCore policy to your newly created role
To attach the IAM role to the EC2 instance, on EC2 Dashboard, select the EC2 instance and modify IAM role.
Select the EC2 instance, click Actions > Security > Modify IAM role
Select the role from the combobox for IAM roles, you have recently created which has the policy AmazonSSMManagedInstanceCore
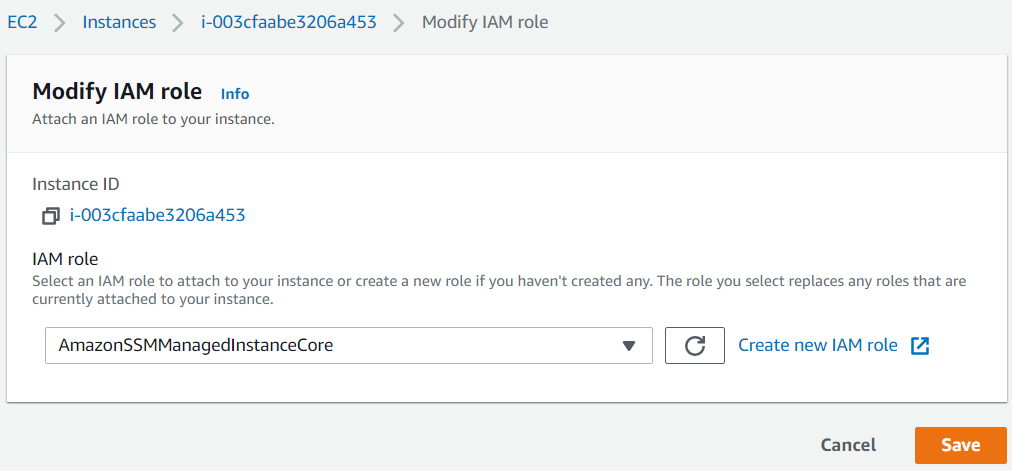
Click Save button to attach the new AWS IAM role to the target EC2 instance.
Now to see if IAM role policy attachment will enable AWS users to connect to EC2 server, again select the EC2 instance and press Connect button.
You will have different options to connect to the target AWS EC2 instance.
We are interested in connecting to EC2 server via Session Manager which does not require any ports (port 22 for SSH nor RDP port 3389)
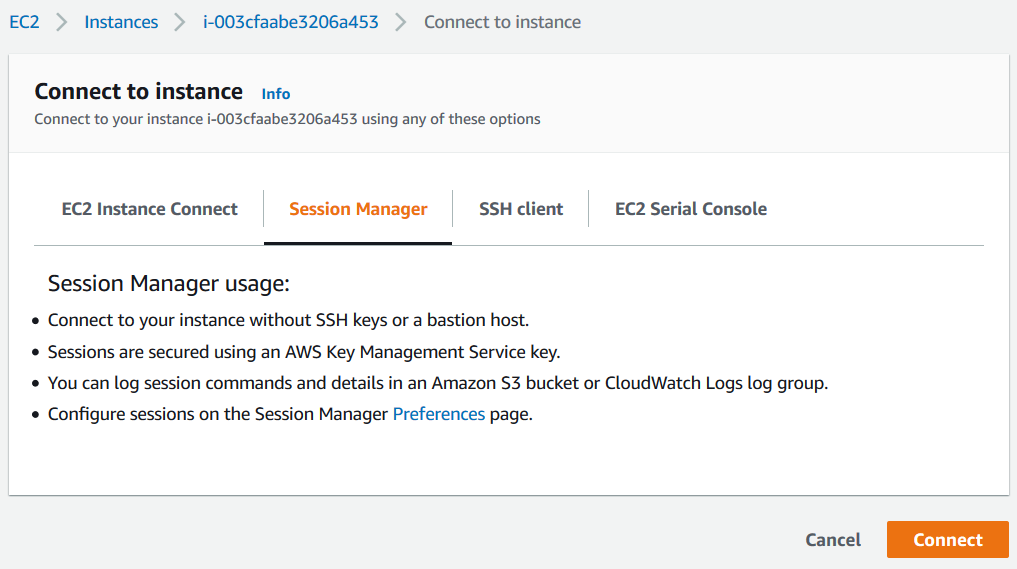
Click Connect button on Session Manager tab to access to remote server via browser.
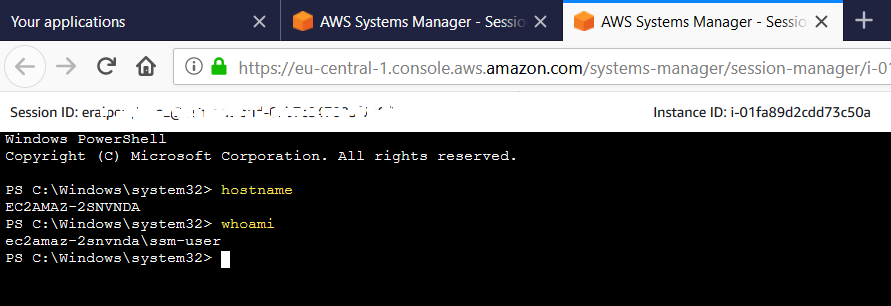
You can see I could connect successfully and executed the "hostname" command on the Linux server on AWS to get the host name which also displaying me the internal IP address of the EC2 instance.
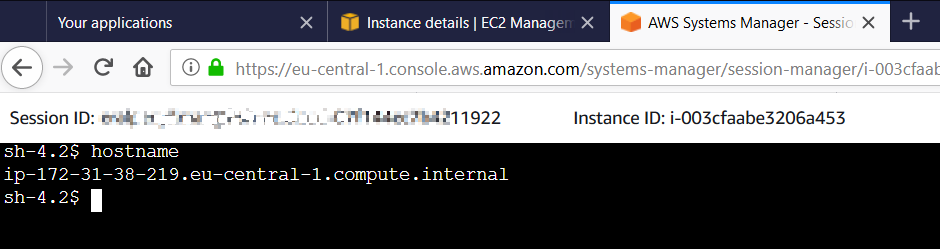
In addition to connect EC2 server from EC2 Dashboard, AWS users can also use the AWS Systems Manager console.
On AWS Systems Manager console, on the left main manu, you will see Session Manager listed under the group Node Management
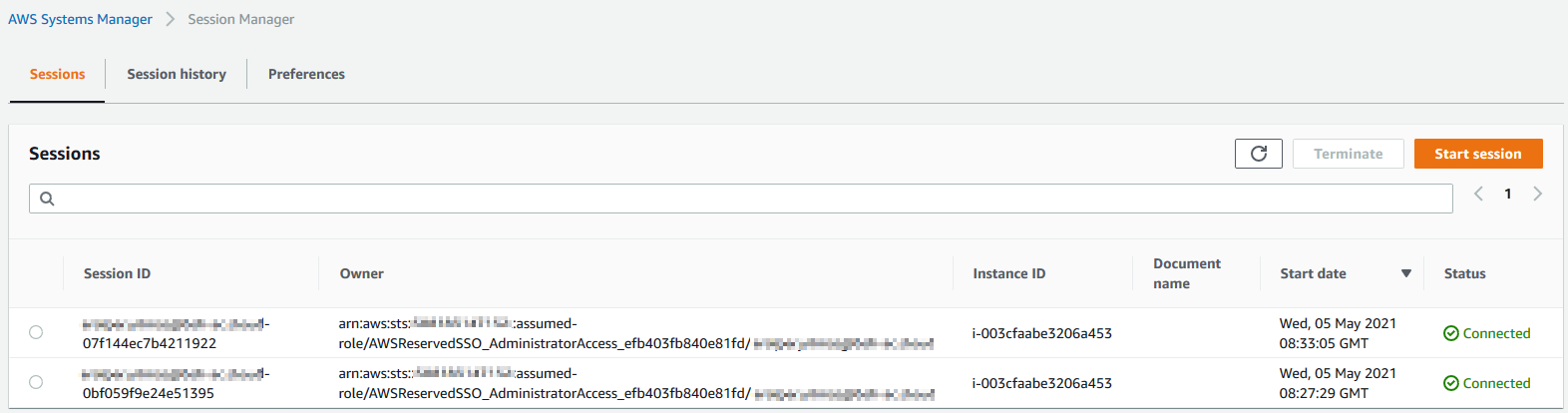
An Session Manager screen, AWS users or operation engineers can see the list of active sessions or can create a new session using the Start session button
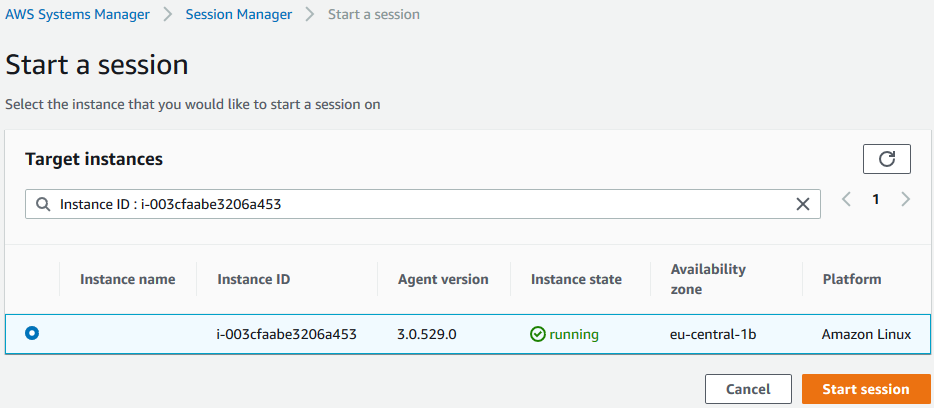
When you click on Start session button, on "Start a session" screen filter to find the target EC2 instance that you want to connect via Session Manager and click on "Start session" to connect via browser.
AWS administrators and users can use the same method to connect to a Windows server.