Attach Policy to IAM Role using AWS CLI Command
If your information technology infrastructure is running on AWS Amazon Cloud Platform, you are already working with AWS IAM service (Identity and Access Management). AWS cloud administrators can use AWS Management Console to manage IAM roles and IAM policies or AWS CLI commands if they are not using Infrastructure as Code approach. In fact using AWS CLI commands to manage you cloud operations on AWS or on any cloud platform, it will make your repeatitive tasks easier to manage. Cloud administrators or engineers can parameterize the AWS CLI scripts and prevent human errors while dealing with cloud operations.
In this AWS tutorials, I want to share how cloud operators can use AWS CLI commands to deal with AWS IAM roles, IAM policies and permissions with sample use cases.
List IAM Policies using AWS CLI Command by Filtering Policy Name
If you need to list IAM policies created in your AWS account, you can use AWS CLI command iam list-policies as shown in following example code.
aws iam list-policies --output json
Of course, executing above AWS CLI command will return all of the IAM policies including AWS managed and customer managed policies existing in your account in a JSON format. Since the list will be too long this is in practical not useful for developers.
Just before we continue with other example usages of the list-policies IAM CLI command, I want to comment on credentials stored in named profiles instead of default profile. If you are using a named profile and stored your AWS credentials in a different profile than the default one, you can modify the above command as follows
aws iam list-policies --output json --profile clouddeveloper
For the rest of the tutorial, I will be using default profile and skip the profile argument in sample commands. In case you are using a named profile, please add your profile name storing your credentials within "--profile profilename"
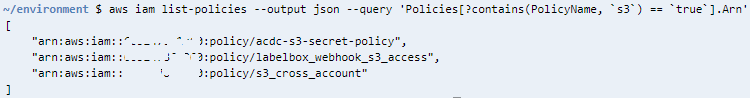
If you need to list IAM policies containing a specific text in their name, please use AWS CLI command iam list-policies with query options illustrated in below sample CLI command. Assume that you are looking for list of IAM policies with name containing the string 's3'
aws iam list-policies --output json --query 'Policies[?contains(PolicyName, `s3`) == `true`]'
Since in my account I have 3 policies created with a name including "s3", the output will be as follows:
[
{
"PolicyName": "acdc-s3-secret-policy",
"PermissionsBoundaryUsageCount": 0,
"CreateDate": "2021-03-10T12:37:25Z",
"AttachmentCount": 2,
"IsAttachable": true,
"PolicyId": "ANPOZLYY5C10ZYJB68ZEYYV",
"DefaultVersionId": "v2",
"Path": "/",
"Arn": "arn:aws:iam::610687860060:policy/acdc-s3-secret-policy",
"UpdateDate": "2021-04-02T07:40:48Z"
},
{
"PolicyName": "labelbox_webhook_s3_access",
"PermissionsBoundaryUsageCount": 0,
"CreateDate": "2021-07-19T15:45:47Z",
"AttachmentCount": 1,
"IsAttachable": true,
"PolicyId": "ANPOZOOY5C10ZYEY68ZEYYV",
"DefaultVersionId": "v1",
"Path": "/",
"Arn": "arn:aws:iam::610687860060:policy/labelbox_webhook_s3_access",
"UpdateDate": "2021-07-19T15:45:47Z"
},
{
"PolicyName": "s3_cross_account",
"PermissionsBoundaryUsageCount": 0,
"CreateDate": "2020-10-19T14:32:43Z",
"AttachmentCount": 0,
"IsAttachable": true,
"PolicyId": "ANPOZOOY5E10YYEY600EYYV",
"DefaultVersionId": "v1",
"Path": "/",
"Arn": "arn:aws:iam::610687860060:policy/s3_cross_account",
"UpdateDate": "2020-10-19T14:32:43Z"
}
]
Please note the account id and polict ids are modified for security purpose
Note that wildcards are not accepted, instead use functions like contains
Since I am only interested in the name of the polices, not interested in policy details, I am changing the above AWS CLI command as below:
aws iam list-policies --output json --query 'Policies[?contains(PolicyName, `s3`) == `true`].Arn'
The output is more simplified compared to previous command execution
[
"arn:aws:iam::610687860060:policy/acdc-s3-secret-policy",
"arn:aws:iam::610687860060:policy/labelbox_webhook_s3_access",
"arn:aws:iam::610687860060:policy/s3_cross_account"
]
It is also possible to format the output as text or table instead of json by replacing output argument value such as shown in following CLI commands
aws iam list-policies --output text --query 'Policies[?contains(PolicyName, `s3`) == `true`].Arn'
aws iam list-policies --output table --query 'Policies[?contains(PolicyName, `s3`) == `true`].Arn'
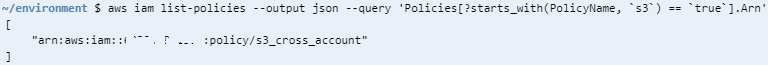
In case you know that the AWS IAM policy that you are searching for starts with a certain string in its name, you can or cloud engineers can replace contains function with starts_with function.
Here how you can use it with a sample case.
aws iam list-policies --output json --query 'Policies[?starts_with(PolicyName, `s3`) == `true`].Arn'
In my AWS account, there is only one IAM policy with a policy name starting with string "s3". The result of the AWS CLI command execution is:
[
"arn:aws:iam::603247861360:policy/s3_cross_account"
]
Get IAM Policy ARN using Policy Name in AWS CLI Command
If the name of the IAM policy is known, to get its ARN to reference the IAM policy in our codes, we can use a different AWS CLI command argument as:
aws iam list-policies --output text --query 'Policies[?PolicyName == `s3_cross_account`].Arn'
This will return the ARN value of the IAM policy.
Instead of returning the ARN value on screen, we can store it in an environment variable
policyArn=$(aws iam list-policies --output text --query 'Policies[?PolicyName == `s3_cross_account`].Arn')
echo $policyArn
![]()
If you are executing AWS CLI commands on PowerShell IDE, the format might change slightly like shown below
$policyArn=(aws iam list-policies --output text --query 'Policies[?PolicyName == `s3_cross_account`].Arn')
echo $policyArn
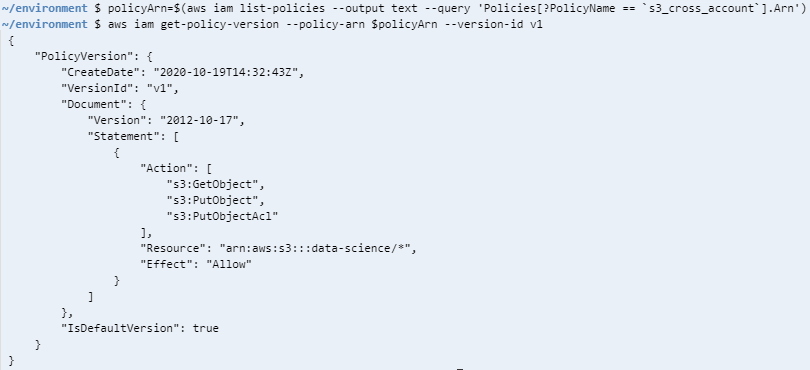
Read IAM Policy Details using AWS CLI Command
Now when we have the IAM policy ARN value, we can use it to display its details to review policy details before we proceed.
This time we will use get-policy-version command option
policyArn=$(aws iam list-policies --output text --query 'Policies[?PolicyName == `s3_cross_account`].Arn')
aws iam get-policy-version --policy-arn $policyArn --version-id v1
Attach IAM Policy to an AWS IAM Role using CLI Command
As the last step we will attach IAM policy to an AWS IAM role using CLI commands.
Cloud engineers can use IAM attach-role-policy command as illustrated in following example code.
Assume that the IAM role that we want to attach our policy is named test-s3-role
policyArn=$(aws iam list-policies --output text --query 'Policies[?PolicyName == `s3_cross_account`].Arn')
aws iam attach-role-policy --policy-arn $policyArn --role-name test-s3-role
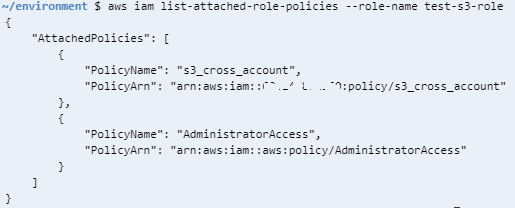
As one last step, we can verify that the IAM policy is successfuly attached to the target IAM role by listing the policies of the role.
Let's list the policies attached to a specific IAM role
aws iam list-attached-role-policies --role-name test-s3-role
To summarize, cloud engineers can use AWS CLI tools in order to manage their daily operations on Amazon Web Services aks AWS cloud platform easily. As shown in this tutorials, AWS CLI tool empowers its users with various API commands including IAM services to manage IAM policies and IAM roles. In this AWS article, I wanted to show how easy it is to add or attach an IAM policy to an IAM role for cloud developers.
